
In our increasingly digital world, the internet brings vast opportunities but also introduces various cybersecurity risks, including different types of web attacks. These cyber threats are constantly evolving, making it crucial to stay updated and vigilant.
As we delve deeper into this article, we’ll shed light on the intricate web of web attacks that pose risks to individuals, businesses, and organizations alike.
- Attackers masquerade as trustworthy entities to deceive users into thinking they are interacting with a legitimate source
- Traffic analysis can help detect and mitigate malicious traffic by distinguishing it from legitimate requests
- Regularly updating and patching DNS servers and practicing good cyber hygiene add an extra layer of protection
- Regular file scans and security audits can help identify and eliminate hidden malicious code
- Educating users about online threats and safe practices is essential
Phishing Attacks

At its core, phishing is a technique that involves luring users into disclosing sensitive information, such as usernames, passwords, credit card details, or other personal data.
Attackers masquerade as trustworthy entities, often imitating well-known brands, institutions, or individuals. The goal? To deceive users into thinking they are interacting with a legitimate source so as to access their data.
The Variety of Techniques
Phishing techniques span a spectrum of complexity and specificity.
Email phishing involves sending fraudulent emails that urge recipients to click on malicious links or download infected attachments.
Spear phishing takes a more personalized approach, tailoring content to a specific individual or organization to increase the likelihood of success. Social engineering exploits psychological vulnerabilities, relying on manipulation and persuasion to trick users into revealing confidential information.
As the digital landscape continues to evolve, phishing attacks remain a constant threat. Educating users about the telltale signs of phishing and fostering a culture of skepticism is paramount to mitigating these risks.
By staying vigilant and equipping oneself with knowledge, individuals, and organizations can stand firm against the deceptive currents of phishing attacks.
SQL Injection Attacks

SQL injection is a cyber attack that leverages vulnerabilities in web applications’ input fields to manipulate the underlying databases. It exploits the lack of proper validation and sanitization of user inputs, enabling attackers to inject malicious SQL queries directly into the application’s database.
The Implications Unveiled
The repercussions of a successful SQL injection attack can be dire. Attackers can gain unauthorized access to sensitive data, alter or delete records, and even take control of the entire database. This compromises user data and erodes trust in the application and the organization.
The Attack Process
Attackers use crafted inputs that manipulate their behavior when executed by the database. This can involve altering queries to expose information not meant to be visible or bypassing authentication mechanisms.
Sometimes, attackers can exploit a single vulnerable input field to compromise the entire database.
Strengthening the Ramparts
Preventing SQL injection attacks requires a multi-pronged approach. Parameterized queries are a vital defense, as they separate user input from the SQL query, rendering injection attempts ineffective.
Input validation further fortifies defenses by rejecting inputs that deviate from expected patterns.
Cross-Site Scripting (XSS) Attacks
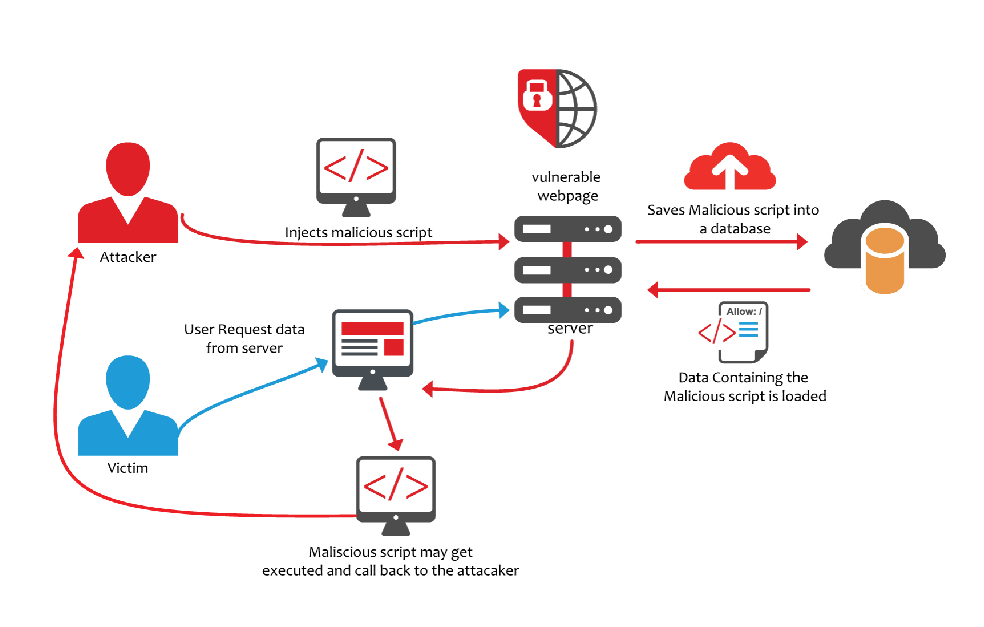
XSS attacks inject malicious scripts into web pages, executed by unsuspecting users’ browsers. These scripts can steal sensitive data, hijack user sessions, or redirect users to fraudulent sites. As web applications dynamically incorporate user inputs, they inadvertently open doors for attackers to manipulate and execute code within the browser.
Variations in Execution
XSS attacks come in various dimensions. Reflected XSS involves malicious scripts embedded within URLs or input fields, executed when the user interacts with them.
Stored XSS occurs when malicious scripts are stored on a server (managed by the web hosting provider) and retrieved by users when they access certain pages.
DOM-based XSS exploits the Document Object Model to inject malicious code directly into the web page’s structure, affecting user interactions.
Defense in the Digital Age
Protecting against XSS attacks demands a proactive approach. Input sanitization serves as a first line of defense, ensuring that user inputs are stripped of potentially harmful code.
However, complete reliance on sanitization can be circumvented by attackers. To counter this, Content Security Policy (CSP) provides an additional layer of defense by defining which content sources are considered safe to execute.
Distributed Denial of Service (DDoS) Attacks
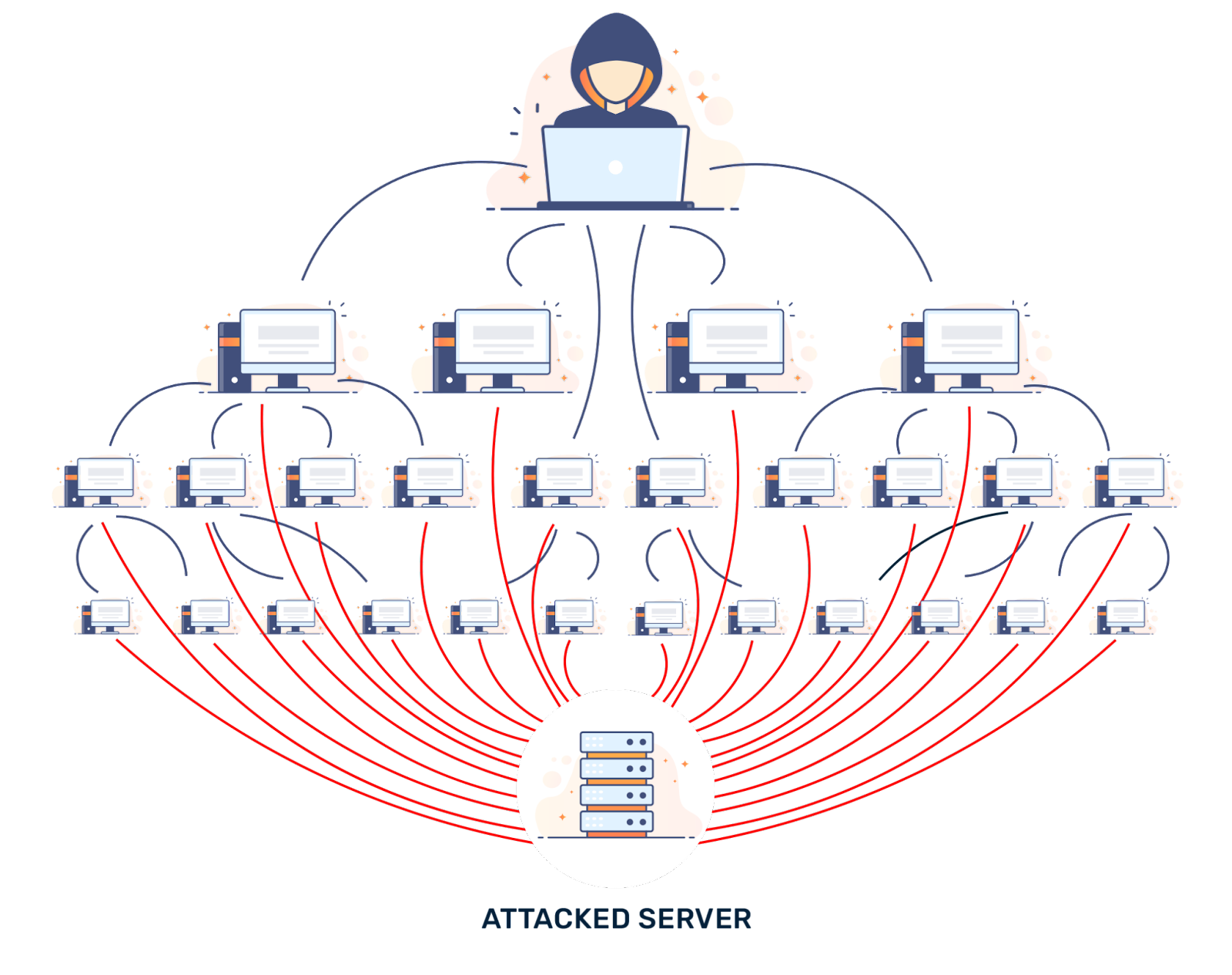
DDoS attacks are orchestrated attempts to overwhelm a target system, network, or website with a flood of traffic.
The aim is to render the target inaccessible to legitimate users by consuming its resources, bandwidth, or processing power to exhaustion.
The Pursuit of Chaos
The objectives of DDoS attacks vary, ranging from ideological motives to financial gains. Hacktivist groups might deploy DDoS attacks to voice their grievances, while cybercriminals leverage them to extort businesses for ransom or to distract from other nefarious activities.
Methods of Onslaught
DDoS attacks employ a variety of methods to achieve their goals. SYN floods exploit the initial stages of a TCP connection by sending a barrage of SYN requests, overwhelming the system’s capacity to handle incoming connections.
Amplification attacks involve sending a small number of requests to publicly accessible servers, which then respond with larger packets to the victim’s IP address, amplifying the attack’s impact.
Shielding Against the Storm
Mitigating DDoS attacks requires a multifaceted approach. Traffic analysis can help detect and mitigate malicious traffic by distinguishing it from legitimate requests.
Employing content delivery networks (CDNs) can distribute traffic across multiple servers, reducing the impact of attacks on any single server.
Man-in-the-Middle (MITM) Attacks
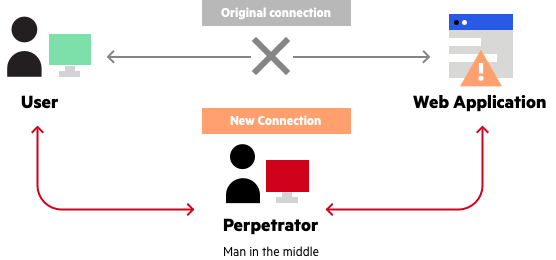
Man-in-the-Middle (MitM) involves an attacker intercepting and potentially altering communications between two parties who believe they are communicating directly.
This covert data manipulation allows the attacker to eavesdrop on conversations, steal sensitive information, or inject malicious content into the exchange.
Walking the Digital Tightrope
Consider a scenario where a user accesses an unsecured public Wi-Fi network. An attacker, positioned between the user and the network, can intercept traffic and gather sensitive data like passwords or credit card information.
In another instance, an attacker might execute a DNS spoofing attack to redirect users to a fraudulent website, convincing them they are interacting with a legitimate source.
The Armor of Defense
MitM attacks emphasize the need for robust defense strategies. Encryption is pivotal in thwarting attackers by ensuring that intercepted data appears gibberish, rendering it useless without the encryption keys.
Implementing secure certificate validation ensures that users communicate with genuine and trusted sources, preventing attackers from masquerading as legitimate entities.
Clickjacking Attacks

Clickjacking or UI redressing involves the artful concealment of malicious content behind seemingly innocent elements on a web page. Users, lured by the legitimate appearance of the visible element, unknowingly interact with the hidden content beneath it.
This deceptive technique tricks users into performing actions they didn’t intend to, potentially leading to unauthorized actions or data exposure.
Tales of Deceit
Imagine a scenario where an innocent-looking button promises a free download or access to premium content. Unbeknownst to the user the button is layered over an invisible iframe containing a form that submits sensitive information. In another case, a seemingly harmless game click could initiate the transfer of funds or divulge personal data.
Fighting the Shadows
Defending against clickjacking attacks requires proactive measures. Frame busting is a technique that prevents a web page from being loaded within a frame, thereby thwarting clickjacking attempts.
Implementing the X-Frame-Options, HTTP header instructs browsers not to render the page within a frame, ensuring malicious actors can’t manipulate content.
Cross-Site Request Forgery (CSRF) Attacks: Manipulating the Strings of Action
Cross-Site Request Forgery (CSRF) attacks exploit users’ authenticated sessions to perform actions without their consent. The attacker crafts a malicious request that, when executed by the victim, triggers an action on a different site where the victim is authenticated.
This leads to unintended and potentially harmful consequences, as the user unwittingly acts on behalf of the attacker.
Unveiling Manipulation
Consider a scenario where a user, authenticated on a banking website clicks a seemingly harmless link on a different site. Behind the scenes, the link transfers funds from the user’s account to the attacker’s.
This manipulation is achieved through the user’s pre-existing session on the banking site without their knowledge.
Fighting Back with Fortifications
Protecting against CSRF attacks requires proactive measures. CSRF tokens are unique tokens generated for each user session and embedded in requests. When the server receives a request, it verifies the token’s authenticity, ensuring the user intentionally initiates the request.
Another defense involves referer header validation, where the server checks the request’s source to ensure it originated from the same site.
Drive-By Downloads

Drive-by downloads are a malicious tactic where users unwittingly trigger the download and installation of malicious software or code simply by visiting a compromised website.
These attacks exploit vulnerabilities in browsers, plugins, or operating systems, taking advantage of users’ trust in legitimate websites.
Trapped in the Web of Intrusion
Imagine opening an article on a seemingly benign website to read an article, not knowing that the website has been compromised. That could expose you to a content whose code has been manipulated to initiate a hidden malware download.
This malware can range from adware and spyware to ransomware, wreaking havoc on the user’s device and potentially compromising their personal information.
Averting the Digital Menace
Averting drive-by downloads necessitates proactive measures. Regular software updates are crucial, often including patches for known vulnerabilities. Disabling unnecessary browser plugins reduces the attack surface, as plugins can be exploited to deliver malicious payloads.
Employing strong antivirus software and enabling browser security features can further fortify defenses against drive-by downloads.
Remote File Inclusion (RFI) and Local File Inclusion (LFI) Attacks
Remote File Inclusion (RFI) involves injecting external files, often malicious, into a web application’s codebase through user inputs.
This allows attackers to execute remote code and gain unauthorized access to the system. Local File Inclusion (LFI) exploits vulnerabilities to include local files, enabling attackers to view sensitive data or execute malicious code from within the server.
The Illusive Goals
The objectives of RFI and LFI attacks vary, from unauthorized data access to full system compromise. Attackers may aim to steal confidential information, deface websites, or even launch more sophisticated attacks by leveraging the compromised system as a foothold.
Exploiting the Gaps
Attackers exploit vulnerable file inclusion mechanisms by manipulating user inputs, such as URLs or form fields. These inputs are used by the application to fetch and display content.
By injecting malicious file paths, attackers trick the application into displaying unauthorized content or executing code.
Shoring Up Defenses
Mitigating RFI and LFI attacks demands a combination of secure coding practices and server configuration. Input validation and sanitization of user inputs help thwart manipulation attempts.
Limiting file inclusion to specific directories and applying access controls ensures that only authorized files are included. Server-side configuration settings should be meticulously adjusted to prevent access to sensitive system files.
Brute Force Attacks

Brute force attacks involve systematically trying all possible combinations of characters until the correct one is found.
Attackers wield the power of automation to iterate through these combinations at high speeds, exploiting the very nature of password and encryption key vulnerabilities.
Cracking the Code
Brute force attacks often target crucial elements like passwords and encryption keys. For instance, an attacker may attempt various combinations of characters to gain unauthorized access to an account.
Similarly, encryption keys to protect sensitive data can be exposed, allowing attackers to decrypt the information.
Defending the Gates
Strengthening defenses against brute force attacks requires proactive measures. Implementing account lockouts after a certain number of unsuccessful login attempts limits an attacker’s progress.
Employing CAPTCHA challenges introduces additional complexity, thwarting automated brute force attempts. It’s crucial to enforce strong password policies that encourage users to choose complex and unique passwords.
Pharming Attacks
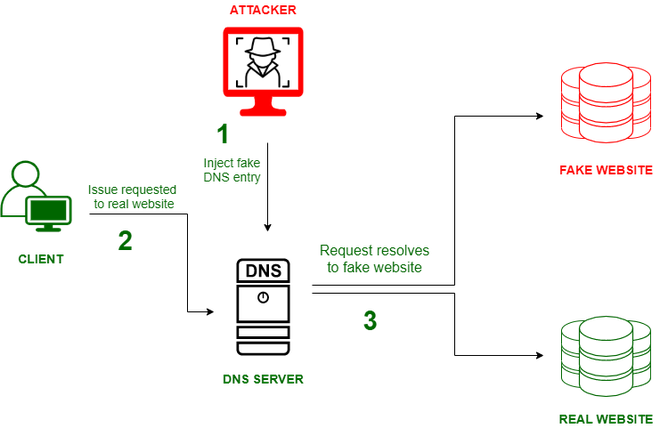
Pharming attacks manipulate Domain Name System (DNS) settings, re-routing users to fraudulent websites without their knowledge. Unlike phishing attacks, which rely on luring users via deceptive emails or links, pharming attacks directly manipulate DNS resolution to poison the digital pathways that guide users to their intended destinations.
Manipulating the Maps
Pharming attackers compromise DNS servers, altering the IP address associated with a legitimate website’s domain name. When users attempt to access the genuine site, they are redirected to a fraudulent counterpart controlled by the attackers.
This malicious mimicry aims to steal sensitive information, such as login credentials or financial details.
Distinguishing Pharming from Phishing
Phishing and pharming differ in their approach. While phishing involves tricking users into voluntarily divulging information through deceptive emails or links, pharming attacks sidestep users’ interaction by hijacking DNS settings, making it harder for users to detect the manipulation.
Bolstering the Defenses
Preventing pharming attacks necessitates a multifaceted approach. Implementing secure DNS configurations and utilizing DNSSEC (DNS Security Extensions) can mitigate the risk of DNS tampering.
Regularly updating and patching DNS servers and practicing good cyber hygiene add an extra layer of protection. Also, educating users about the dangers of pharming and how to identify suspicious activity enhances their ability to recognize potential threats.
Session Hijacking (Session Fixation)
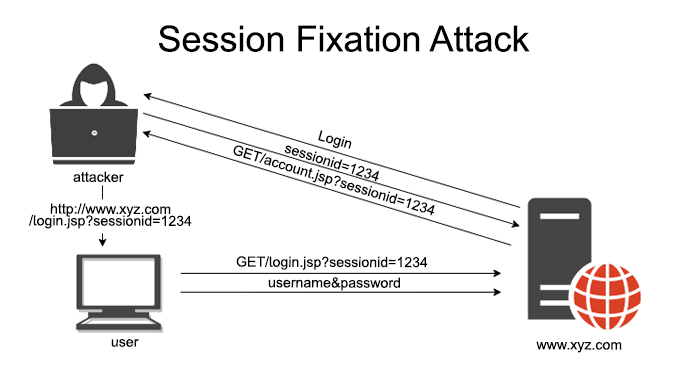
Session hijacking involves unauthorized individuals gaining control over an active user’s session, granting them access to sensitive data and functionalities.
Session fixation, on the other hand, manipulates users into establishing sessions with predetermined credentials, thereby enabling attackers to exploit their active sessions.
Exploiting the Open Door
Attackers exploit various techniques to carry out session hijacking. Session sniffing involves intercepting session data during transmission, enabling attackers to impersonate users.
Session-side jacking targets unencrypted session cookies, which can be intercepted and used to gain unauthorized access.
Mitigating the Threat
Mitigating session hijacking and fixation requires robust security practices. Employing HTTPS encrypts data transmission, making it difficult for attackers to intercept sessions.
Utilizing secure session management practices, such as expiring sessions after a certain period of inactivity, helps minimize the window of opportunity for attackers.
Implementing unique session IDs that change with each login ensures that attackers can’t predict or fixate on session credentials.
Malware Injection
Malware injection involves surreptitiously embedding malicious code into legitimate websites. Attackers exploit vulnerabilities in websites’ codebases, plugins, or third-party components to inject the malicious payload. This allows the attacker to compromise visitors’ devices or manipulate the website’s functionality.
Planting the Seeds of Chaos
Once the attacker succeeds in injecting malware, the consequences are far-reaching. For website visitors, the malware can lead to device infections, data theft, or unauthorized activities.
For website owners, the fallout includes reputation damage, loss of user trust, and potential legal liabilities. Additionally, search engines might flag infected websites, impacting their visibility and traffic.
Fortifying the Digital Stronghold
Preventing malware injection demands a multi-pronged approach. Regular file scans and security audits can help identify and eliminate hidden malicious code. Implementing strict input validation checks on user inputs to prevent malicious data from being processed.
Adhering to secure coding practices and keeping software updated minimizes vulnerabilities.
XML External Entity (XXE) Attacks

XML External Entity (XXE) attacks exploit XML parsers’ ability to include external entities, external resources like files or URLs, into XML documents. Attackers manipulate poorly configured XML parsers to process these external entities, opening the door for unauthorized data retrieval and potential system compromise.
Exposing the Underbelly
The risks posed by XXE attacks are far-reaching. Attackers can exploit XXE vulnerabilities to access sensitive data stored on the server. This includes confidential user information, database content, and even system files.
Data exposure through XXE attacks compromises privacy and lays the groundwork for further exploitation.
Building Digital Ramparts
Preventing XXE attacks requires proactive measures. Disabling external entity processing in XML parsers eliminates the avenue of attack.
Additionally, implementing input validation ensures that user-supplied XML data doesn’t contain malicious payloads. Utilizing parsers that offer sandboxing or whitelisting capabilities can further fortify defenses against XXE attacks.
Server-Side Request Forgery (SSRF)
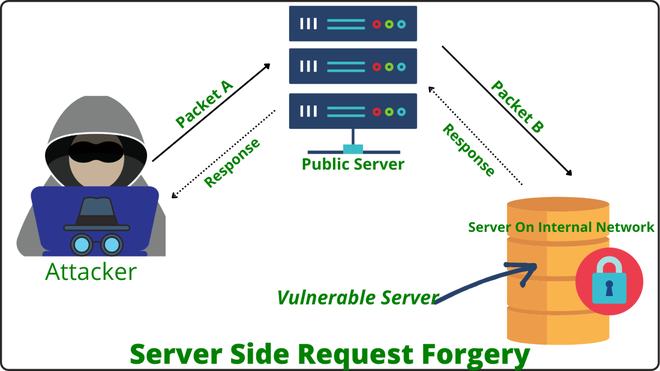
Server-Side Request Forgery (SSRF) attacks manipulate servers into making requests to other internal or external resources on behalf of the attacker. These requests are often masked to appear as if they originate from the server.
By exploiting this deception, attackers can trick the server into accessing unauthorized data or resources, often leading to unintended consequences.
Unveiling the Ripples
The impact of SSRF attacks extends beyond unauthorized data access. Attackers can use SSRF to gain access to internal systems, enabling them to retrieve sensitive data, interact with restricted APIs, or even launch further attacks.
Additionally, SSRF can be leveraged to bypass firewalls or network security measures, compromising the network’s overall security posture.
Guarding Against Subterfuge
Preventing SSRF attacks requires a multi-layered approach. Implementing strict input validation ensures that user-supplied URLs cannot be manipulated to access unauthorized resources.
Whitelisting URLs restricts server requests to approved destinations, reducing the attack surface. Employing network segmentation isolates critical systems from public-facing servers, limiting the potential impact of a successful SSRF attack.
Protecting Your Site Against Web Attacks: How to Do It
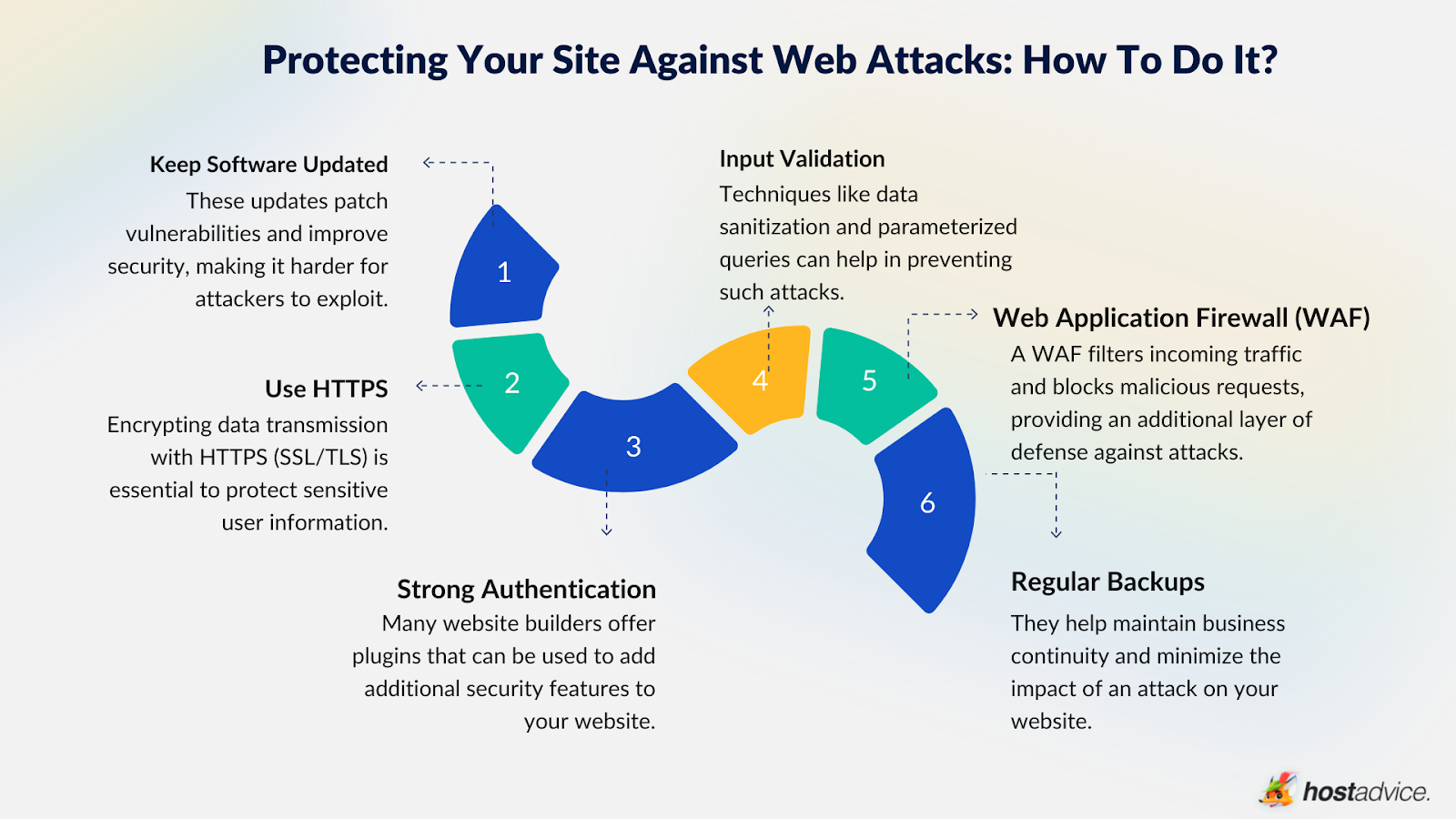
Keeping your website secure is paramount to maintaining its integrity and reputation. Here’s a comprehensive guide on how you can protect your site from web attacks:
Keep Software Updated
Regularly updating your operating system, web server, content management system (CMS), plugins, and libraries is crucial. These updates patch vulnerabilities and improve security, making it harder for attackers to exploit weaknesses.
Use HTTPS
Encrypting data transmission with HTTPS (SSL/TLS) is essential to protect sensitive user information. HTTPS ensures that data transmitted between the user’s browser and your website is encrypted and cannot be intercepted.
Strong Authentication
Multi-factor authentication (MFA) adds an extra layer of security to user accounts. It involves using authentication methods such as passwords, biometrics, or security tokens to enhance security.
Many website builders offer plugins that can be used to add additional security features to your website.
Input Validation
Input validation prevents attacks like SQL injection and cross-site scripting by validating user data. Techniques like data sanitization and parameterized queries can help in preventing such attacks.
Web Application Firewall (WAF)
A WAF filters incoming traffic and blocks malicious requests, providing an additional layer of defense against attacks. It can also help detect and block attacks like SQL injections and cross-site scripting.
Regular Backups
Regular backups are crucial for data recovery in the event of an attack. They help maintain business continuity and minimize the impact of an attack on your website.
User Education
Educating users about online threats and safe practices is essential. Creating user awareness and providing tips for recognizing phishing attempts can help prevent attacks.
Content Security Policy (CSP)
A CSP controls content execution and prevents attacks like cross-site scripting. It can also help in enforcing data privacy and security policies.
Security Headers
HTTP headers can enhance browser security by adding additional security-related information. Commonly used headers like X-Frame-Options, X-XSS-Protection, and X-Content-Type-Options can help prevent attacks.
Monitoring And Intrusion Detection
Setting up monitoring and intrusion detection systems can help identify and respond to suspicious activity in real time, minimizing the impact of an attack on your website.
By implementing these measures, you can protect your website from web attacks and ensure it remains secure and trustworthy.
Conclusion
In the ever-evolving landscape of web attacks, safeguarding your digital presence remains an ongoing pursuit. The strategies outlined in this guide empower you to fortify your website against many threats.
By implementing these measures, you establish a robust defense that stands as a bulwark against the relentless tide of cyber adversaries.
Next Steps: What Now?
As you embark on your journey to fortify your website’s defenses, consider taking these practical next steps:
- Implement Security Measures: Implement the strategies discussed in this guide, from regular updates to strong authentication.
- Stay Informed: Stay abreast of the latest trends in cyber threats and defense strategies to adapt and evolve your security posture.
- Educate Your Team: Share your newfound knowledge with your team and users, creating a united front against potential attacks.
- Regular Audits: Conduct security audits to identify and address vulnerabilities promptly.
- Select a reliable and secure Web Hosting Provider
Further Reading – Useful Resources
Expand your understanding of cybersecurity and website protection with these valuable resources:
- Website Security: From Basics to Advanced Measures
- Web Hosting Security Guide
- Six Security Features Your Web Hosting Provider Must Have
- WordPress Security Guide: How to Defend Your WordPress Site
- What Is DDoS?
- PHP Session Security: How to Avoid Session Hijacking
- Varnish Cache Acceleration
- Encryption and PHP Git Server Attack
- Compromised High-Traffic Sites



